How to Fortify Your Docker Containers: A Guide to Advanced Security Practices
Introduction
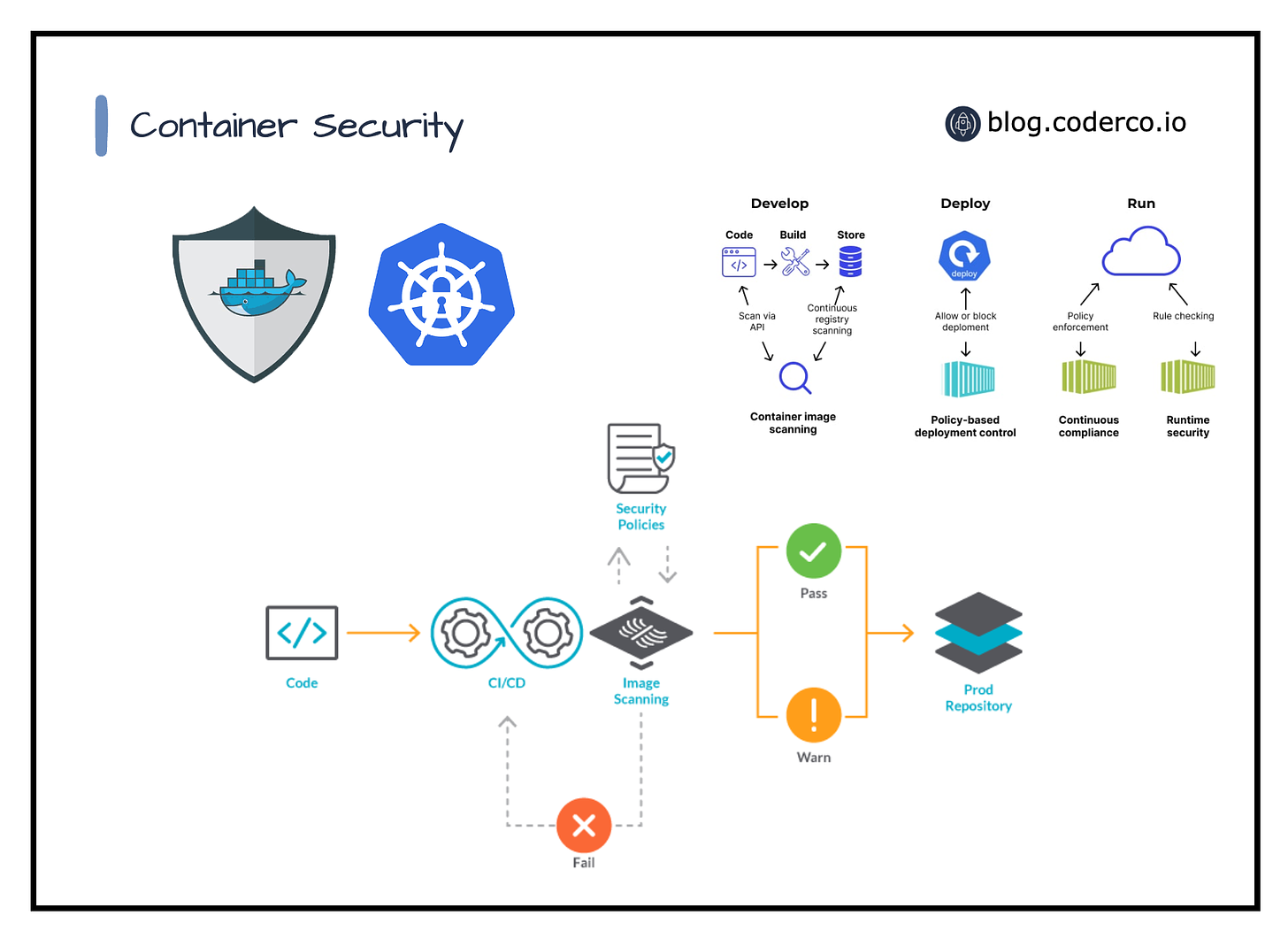
DevOps has been rapidly evolving in the software development landscape, and from the cornerstone Docker has emerged. Its ability to package applications into portable, scalable containers has taken deployment strategies to the next level. However, with this power, comes the responsibility of securing the containers. In this blog, we dive deep into advanced techniques and best practices for securing Docker containers, ensuring your deployments are not just efficient but also fortified against a variety of cyber threats.
We will cover the following:
Securing container images
Vulnerability scanning and management
Post-deployment? Runtime container security
Docker in CI/CD pipelines
Continuous security monitoring and feedback loops
Real-world scenario - securing containers in a CI/CD workflow
In short, this blog is not just a guide; it’s a journey into the depths of Docker container security. So I hope by the end of this blog, you will be equipped not just with knowledge but with practical, actionable strategies to fortify your containers against the never-ending cyber threats.
Quick Reminders:
Join our 10-hour Linux Course waiting list ➡️ Waiting List!
Subscribe to our YouTube Channel, we are currently working on something, click on the 🔔 so you don’t miss out: CoderCo
Building Secure Docker Images
When it comes to Docker, the image is everything - literally. It’s the blueprint of your application, dictating how it will run in various environments. But not all Docker images are created equal, especially if we look at it from a security standpoint. Let’s dissect how to build secure Docker images, spotlighting common pitfalls and showcasing better practices.
The Not-So-Great Dockerfile
First, let's look at an example of what you might call a 'less-than-ideal' Dockerfile. It's common, maybe a bit too common, in the wild:
# Example of a suboptimal Dockerfile
FROM ubuntu:latest
RUN apt-get update && apt-get install -y python3 python3-pip python3-dev
COPY . /app
WORKDIR /app
RUN pip3 install -r requirements.txt
CMD ["python3", "app.py"]
At first glance, it seems okay, right? But let's break it down:
Using
ubuntu:latestas a base image. It's like rolling the dice with security.Installing unnecessary packages (
python3-dev), adding to the attack surface.No specific user is defined, meaning the container might run with root privileges.
The Improved Dockerfile
Now, let's refactor this Dockerfile with security in mind:
# Example of a more secure Dockerfile
FROM python:3.9-slim
RUN useradd -m dockeruser
WORKDIR /home/dockeruser
COPY . .
RUN pip install --no-cache-dir -r requirements.txt
USER dockeruser
CMD ["python", "app.py"]
Why is this one better?
We're using
python:3.9-slimas a base image. It's leaner and more secure.We create a non-root user (
dockeruser) and switch to it. No more running as root!The
-no-cache-dirflag with pip prevents caching unnecessary files.
Key Takeaways
Choose the Right Base Image: Opt for slimmer, more secure base images that contain only what you need.
Avoid Running as Root: Always create and switch to a non-root user in your Dockerfile.
Minimize Layers and Build Cache: Keep your images lean. Unnecessary layers and cached data can be a haven for vulnerabilities.
Remember, building a secure Docker image is like laying a strong foundation for a house. It's a crucial first step in ensuring the security of your containerized applications.
Vulnerability Scanning and Management
A crucial checkpoint in container security is vulnerability scanning and management. It’s not just about building secure containers; it’s also about continuously monitoring them for vulnerabilities. This process is akin to a routine health check-up for your container images, ensuring they are always in top-notch security shape.
The Vital Role of Vulnerability Scanning
Imagine your Docker containers as constantly evolving entities. Each change, addition, or update potentially opens the door to new vulnerabilities. That's where vulnerability scanning steps in - it's a measure against these evolving threats.
Several tools can help you in this mission:
Clair: Known for its static analysis capabilities, Clair is a robust choice for scanning container vulnerabilities.
Trivy: Praised for its simplicity and comprehensiveness, Trivy scans containers and other artifacts for vulnerabilities.
Docker Bench for Security: This tool focuses on best practices for deploying Docker containers securely.
Integrating Vulnerability Scanning with GitHub Actions
Integrating vulnerability scanning into your CI/CD pipeline is essential. Let's demonstrate how you can incorporate Trivy scanning within a GitHub Actions workflow:
name: CI
on: [push]
jobs:
trivy_scan:
runs-on: ubuntu-latest
steps:
- name: Check out the repo
uses: actions/checkout@v2
- name: Set up Docker Buildx
uses: docker/setup-buildx-action@v1
- name: Login to DockerHub
uses: docker/login-action@v1
with:
username: ${{ secrets.DOCKERHUB_USERNAME }}
password: ${{ secrets.DOCKERHUB_TOKEN }}
- name: Build and push Docker image
uses: docker/build-push-action@v2
with:
context: .
push: true
tags: yourdockerimage:tag
- name: Run Trivy vulnerability scanner
uses: aquasecurity/trivy-action@master
with:
image-ref: 'yourdockerimage:tag'
format: 'table'
exit-code: '1'
This GitHub Actions workflow automatically checks out your code and runs Trivy against your Docker image on every push to the repository. If Trivy finds any vulnerabilities, the action will fail, alerting you to take necessary actions.
Why Continuous Assessment Matters
In the world of container security, you cannot be complacent. Continuous vulnerability assessment ensures that your security measures evolve with emerging threats. Integrating these scans into your CI/CD pipeline via tools like GitHub Actions ensures that every new build is vetted for security vulnerabilities before it hits production.
Advanced Runtime Container Security
Having established a solid foundation with secure Docker image creation and continuous vulnerability scanning, it's time to focus on the runtime environment. Advanced runtime container security is about ensuring that once your containers are up and running, they continue to operate in a secure and isolated manner.
Container Isolation and Segregation
Isolation is a fundamental principle in container security. Docker achieves this through mechanisms like namespaces and control groups (cgroups) - you might know this if you have a good Linux background.
Namespaces: Docker uses namespaces to provide each container with its own isolated workspace, including its own network, process ID space, mount points, and inter-process communication (IPC) resources.
Cgroups: Control groups limit and allocate resources such as CPU, memory, network bandwidth, and disk I/O among a group of processes. This prevents any single container from exhausting system resources.
Implementing Security Best Practices for Isolation
Network Segregation: Use Docker's network drivers to create separate networks for different containers or groups of containers, minimising the risk of a compromised container affecting others.
Read-only Filesystems: Where possible, run containers with read-only filesystems using the
-read-onlyflag. This can prevent malicious processes from writing to the filesystem.Use of User Namespaces: Enable user namespaces to map users inside a container to different users on the host system, thereby limiting the impact of a container compromise.
Implementing Resource Limits
Managing resource limits is not just a matter of performance, but also of security. Unrestricted resource usage can lead to DoS (Denial of Service) attacks.
Setting Container Resource Limits
Use Docker's resource management features to set limits on a container's use of system resources:
Memory Limits: Use the
mor-memoryflag to limit a container's memory usage.CPU Limits: Use the
-cpusflag to limit the number of CPU cores a container can use.
For example:
docker run -it --memory=500m --cpus="1.5" ubuntu:latest /bin/bash
This command runs an Ubuntu container with a maximum of 500 MB of memory and 1.5 CPU cores.
Security Benchmarks: The CIS Docker Benchmark
A key aspect of runtime container security is adhering to established security benchmarks. The CIS Docker Benchmark, provided by the Center for Internet Security, is a widely recognised standard for securing Docker containers.
Implementing the CIS Docker Benchmark
Container Image Assurance: Ensure only trusted base images are used, and enforce vulnerability scanning.
Container Runtime Security: Apply runtime security measures like network segmentation, resource limits, and audit logging.
Host Security Configuration: Secure the host system running Docker, adhering to host-level security benchmarks.
In summary, advanced runtime container security is about ensuring your containers not only start securely but continue to operate securely within their runtime environment. By implementing isolation, and resource limits, and adhering to security benchmarks like the CIS Docker Benchmark, you can significantly enhance the security posture of your containerised applications.
A real-world scenario
Let’s now explore a real-world scenario that illustrates the implementation of container security in a CI/CD pipeline. This case study is based on a mid-sized tech company, which we'll call "CoderCo," that adopted Docker containers for their application deployments.
Background
CoderCo had a robust CI/CD pipeline but initially overlooked the security aspects of their containerised applications. As they scaled, they faced challenges with managing vulnerabilities in their Docker images and ensuring secure deployments.
Challenge
The primary challenge for CoderCo was integrating security measures into their existing CI/CD workflow without disrupting their deployment speed. They needed a solution that would automatically scan for vulnerabilities, enforce security best practices, and provide real-time security monitoring.
Solution
Automating Vulnerability Scanning: CoderCo integrated Trivy into their GitHub Actions pipeline. This tool automatically scanned new Docker images for vulnerabilities during the build phase. If critical vulnerabilities were detected, the deployment was halted.
Implementing Security Benchmarks: They adopted the CIS Docker Benchmark, ensuring their Docker configurations adhered to industry-standard security practices.
Ensure a user for the container: They modified Dockerfiles to include a non-root user for running the container processes.
Enable Docker Content Trust: They enforced image verification by setting the
DOCKER_CONTENT_TRUSTenvironment variable.Limit Container Resources: Resource limits (CPU, memory) were set for each container to mitigate DoS attacks.
Audit Docker Files and Directories: Regular audits were scheduled for Docker daemon files, directories, and configurations.
Continuous Security Monitoring: TechFlow set up Prometheus and Grafana for real-time monitoring of their container environments. They monitored metrics like container resource usage, network activity, and unexpected behaviour patterns.
Implementation Example
Here's an example Dockerfile change implementing non-root user:
# Original Dockerfile
FROM nginx:latest
COPY . /usr/share/nginx/html
# Modified Dockerfile with CIS Benchmark
FROM nginx:latest
RUN useradd -m dockeruser
USER dockeruser
COPY . /usr/share/nginx/html
To enforce Docker Content Trust, they added the following to their CI/CD pipeline script:
export DOCKER_CONTENT_TRUST=1
docker build -t secureapp .
Results
After implementing the CIS Docker Benchmark:
There was a notable decrease in configuration-related vulnerabilities.
The team gained better insight into Docker security best practices.
The automated enforcement of these benchmarks added a robust layer of security without adding manual overhead.
Lessons Learned
Incremental Implementation: It's more effective to implement security benchmarks incrementally rather than trying to overhaul the system all at once.
Employee Training: Educating the team about the importance of these benchmarks was crucial for smooth implementation.
Continuous Review: Regularly reviewing and updating the configurations according to the latest benchmark versions helped maintain a high security standard.
Implementing the CIS Docker Benchmark significantly enhanced the security posture of CoderCo’s Docker environment. This case study highlights the practicality and effectiveness of following industry-standard benchmarks to secure Docker containers.
Conclusion
To conclude our exploration of the advanced techniques and best practices for securing Docker containers, we must remember it’s a continuous journey. The landscape of container security is continously evolving; so we must also evolve the techniques we use.
The key takeaway from our dicussions is the importance of ongoing vigilance. Security is not a one-time setup; it’s a continous process of monitoring, updating, and adapting to new threats and vulnerabilities.
So it’s essential to stay informed about the latest security trends, tools, and threats. Continuous learning and adaptation isn’t a recommendation…it’s NECESSARY for maintaining robust security practices.
Summarising Key Points:
Secure Docker Images: Start with creating secure Docker images, focusing on minimalism and the principle of least privilege.
Vulnerability Scanning and Management: Integrate continuous vulnerability scanning in your CI/CD pipeline to catch issues early.
Runtime Security: Implement advanced runtime security measures like container isolation, resource limits, and adherence to security benchmarks like the CIS Docker Benchmark.
CI/CD Security Integration: Embed security checks into your CI/CD pipeline to ensure continuous delivery of secure applications.
Continuous Monitoring and Feedback: Establish monitoring and feedback mechanisms for ongoing security assessment and improvement.
Final Thoughts
As Docker continues to play a critical role in modern DevOps, the responsibility of securing containers becomes increasingly significant. By adopting the practices and techniques we discussed, you can ensure that your containers are not just efficient and scalable, but also secure and resilient against the cyber threats in the digital world.
Remember, the path to securing Docker containers is ongoing. Stay curious, stay informed, and continually adapt your security practices to navigate this ever-changing landscape successfully.